Unmanaged APIs are considered one of modern-day enterprises’ largest safety risks. The common API security breach prices $6.1 million and is predicted to almost double by 2030. The OWASP Top 10 (Open Web Application Security Project) is an inventory of the ten worst vulnerabilities, ranked in accordance with their exploitability and impact.
Api With Out Authentication: Risks And Options
- But these APIs can still turn out to be an assault vector into a system, permitting malicious customers to not directly send problematic inputs, corresponding to SQL injections or solid URLs.
- SOAP (simple object access protocol) is a protocol for exchanging structured data in the implementation of internet services in pc networks.
- It’s not a regular or protocol, however quite a set of architectural constraints.
- Regularly replace and in addition have to patch APIs to fix known vulnerabilities and maintain a safe API infrastructure.
- Misconfigurations and safety holes typically outcome from poor design or incremental patching over time.
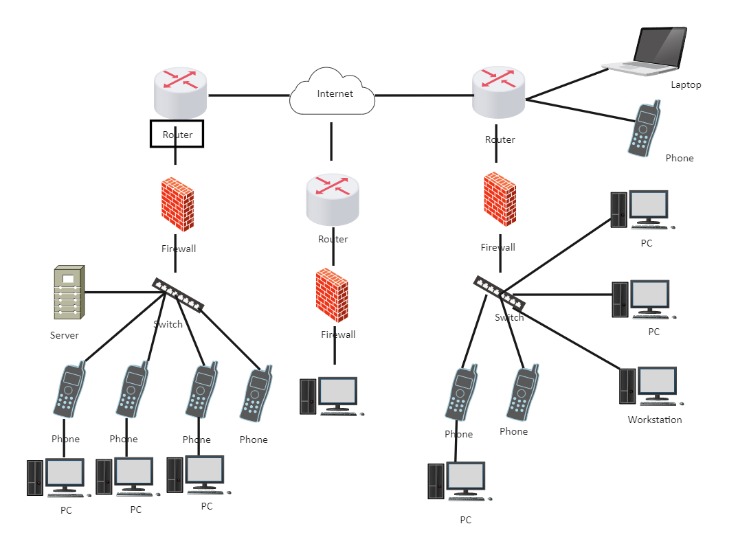
This is one cause we’re seeing a shift in direction of AVA.HOSTING the Zero Trust security model, which shifts from applying safety on the enterprise perimeter to security at the API layer. In the digital world, authentication is the method of verifying a user’s identification. It essentially pulls off the masks of anybody who desires to see your data. Continuous monitoring and logging of API activity are crucial for identifying safety incidents and guaranteeing compliance with safety insurance policies.
Written By Api Professional
Yet, if each team implements their very own JWT validation resolution, you threat growing general system vulnerability. Zero-trust is not just a buzzword — your API ought to limit belief to incoming traffic. One of the steps towards constructing zero-trust is using HTTPS for all API traffic. If attainable, use HTTPS internally so that visitors between providers cannot be sniffed.
When a consumer logs in, they’re given a JWT which they will then use to make authenticated requests to the API. The JWT will contain information about the user, such as their name and ID. JWTs may additionally be used to protect data that’s being saved on the shopper. For instance, a JWT can be used to encrypt the contents of a cookie.

